C4SS supports access to this site directly through the Tor network as an Onion Service. Practically, this means that if you visit the address vhgli4v7feaaz7ka.onion through the Tor Browser you will see the content of c4ss.org, but without your request to our server ever leaving the onion encryption of the Tor network. You can download the Tor Browser here.
If you believe, as we do, that Tor is one of the technologies that makes both state and corporate oppression not only obsolete, but impossible, please consider donating to the Tor Project or operating as a Tor relay.
The State is damage, we will find a route around!
- C4SS Now Available Directly as a Tor Onion Service
- Internet Security Is Our Responsibility
- Tools and tactics for your digital security
- Tor: The Onion Router
- Tor Is For Everyone: Why You Should Use Tor
- 7 Things You Should Know About Tor
- Using PGP Encryption To Communicate Privately
- Keeping Your Cryptocurrency Safe
- Dark Wallet: New Weapons for Old Wars
What is Tor? How does it work? And why should you use it?
With the ever expanding surveillance systems being employed in the United States and around the world, the ability to use the internet anonymously is becoming increasingly important, especially for activists, or anyone who is not okay with your Search Engine provider, ISP (Internet Service Provider) and your government knowing everything about your internet use. Here, I will go into brief detail about the technical aspects of Tor, give reasons why you should use Tor and finally guide you through the installation of the Tor browser and how to contribute to the network by setting up a relay.
What is Tor?
Tor, formally an acronym for “The Onion Router“, is a distributed proxy network designed to provide anonymity on the web. Much like a VPN (Virtual Private Networks). Tor encrypts your traffic and bounces it through a number of relays before arriving at it’s destination. Preventing third parties from being able to see what you are sending through the network, and where your traffic initially came from. Tor can also be used for servers, to anonymize the physical location of websites, and those who visit them.
How does it work?
There are a number of very in depth resources that explain in a lot of detail how the network works, this is not that. This is a brief guide to introduce you to the concept of onion routing, and if you wish to learn further, there will be a number of links included.
When you attempt to contact a website using the Tor Browser, the Tor client randomly selects 3 nodes from the network. The client then encrypts a message to be sent to the final recipient (e.g a website you want to visit). The encrypted message is sent to the first node, the first node then peels off an initial layer of encryption, revealing where to send the message to the second node, this process is repeated until it reaches the third and final node, also known as the “exit relay”, where the message is unencrypted and sent to the final recipient. The effect of this is to obscure your IP address from the destination server by providing multiple barriers between you and the server. Keep in mind however, personal information that you choose to give to a website, such as in a sign up form, is treated like any other data by the website, it can be looked at by an administrator, or subpoenaed by Law Enforcement, Tor works most effectively if you keep your information private as well as anonymous.
Why should you use it?
Increasingly, governments around the world have become preoccupied with what is known as Total Information Awareness, the ability to track every piece of digital information that we create: financial transactions, instant messages, email, web history, etc. This information can be used to intimidate, harass, or even jail dissidents, journalists and those who may pose some form of nuisance to the government. Many nations have strong controls on what people can search for and view on the internet. Tor allows for the bypassing of these filters, and has been especially useful in Iran, a nation which enjoys extremely high usage of the Tor network.
In the short term, there is little we can do to stop this encroaching surveillance state. But we are able to protect ourselves and others by obscuring as much data as possible. Tor is one such solution. The more people who use Tor, among other things, to browse the web, when they feel it necessary, the less useful our data will be to the government. The more of us who run relays for the Tor network, the faster the system will function for those who need to use it.
Setup
In recent times, attention has been paid to making the use of Tor extremely easy for the less technically proficient, with minimal setup required. The Tor browser bundle can be downloaded from here:
This will install the components needed to use the Tor network, including a modified version of Firefox specifically configured for Tor and Vidalia, a graphical front-end that will allow you to configure your Tor settings, including setting up a relay to contribute to the network.
If you do not feel the need to use the Tor browser on your system, but wish to set up a Tor relay, the package can be downloaded by following this link, choosing your operating system, then choosing the Tor Relay Bundle. This will be especially useful on desktop computers, or dedicated computers that run constantly. While a temporary relay does not harm the network, a permanent one is much more useful. When you run a relay from your system, you will be making the Tor network larger and faster. By adding a node, you make the network more distributed, providing for more robust anonymity. You are also spreading the traffic load, increasing the speed of the network.
The Tor Relay bundle can be downloaded from here:
- https://www.torproject.org/download/download.html.en – Choose your operating system, then “Tor Relay Bundle”.
Setting up the browser is simple, just download the file, extract it to the folder of your choice, then click the “Start Tor Browser” in the folder. Vidalia should start to run, and once it is connected to the network, the browser will open and will notify you if you are successfully running Tor.
If you wish to run a relay along with the browser, go to “set up relay” in Vidalia and check “relay traffic inside the Tor network (non exit relay)”, set how much bandwidth you wish to donate and you are good to go.
If you have installed the relay bundle, the relaying option should be set up automatically, and Vidalia will attempt to run whenever you boot your computer. You may wish to run as an exit relay, but do so at your own risk. If you run as an exit relay, your IP will be what the destination websites see when someone uses your relay, the traffic runs unencrypted from your connection to the destination, and if someone is using Tor for less than savory purposes; spamming, Wikipedia vandalism, child pornography, etc. You run the risk of having your IP banned from many websites due to actions of others, have your computer seized or even be arrested by law enforcement. If you wish to run an exit node, please follow this guide from the Tor Project to mitigate the risks involved. I must emphasize however, these are not issues if you run a relay inside the network, as all traffic you send and receive will be encrypted.
I hope this guide has been useful and convinced those not already using Tor to give it a try.
There are further resources available for a more in depth look at:
- https://www.torproject.org/docs/faq.html.en
- https://www.torproject.org/dist/manual/short-user-manual_en.xhtml
- https://trac.torproject.org/projects/tor/wiki
Using PGP Encryption To Communicate Privately
There are many tools out there that allow you to communicate privately with varying levels of security. PGP (Pretty Good Privacy), specifically the OpenPGP standard, is a well tested and solid method of encrypting emails and messages, before transmission, to ensure that the only person who can read them is the intended recipient. I need not reiterate the importance of privacy, especially for activists in different regions around the world, including the USA, where domestic spying can and has been used to attempt to thwart activist groups. PGP is a reliable standard and the one used by Edward Snowden in his communications with Glenn Greenwald.
PGP relies on what is called “Public Key Cryptography” to cipher and decipher messages. In times gone by, to send cryptographic messages to a recipient, an agreed upon key or method would need to be shared beforehand. This may have required meeting with the recipient in person to establish the “key” without fear of interception. If an encrypted letter was likely to be intercepted, it is just as likely that a letter detailing a secret decryption algorithm would be intercepted. This situation is clearly impractical in the current state of mass communication across the world with people you cannot easily meet in person.
Public Key Cryptography, or Asymmetric Key Cryptography, is a solution to this problem. First both parties wishing to engage in an encrypted conversation must generated key pairs. Each participant will generate a public and a private key using their PGP software (this only needs to be done once per person). The public key is the cipher. This is the key used to encrypt a message. The private key, which is mathematically related to the public key, is used to decipher the message. In reality, a symmetric session key is generated to encrypt each message. The session key itself is then encrypted with the public key and sent within the message.
How this works, practically,
- Person A shares their public key with Person B.
- Person B uses this key to encrypt a message and send it back to Person A.
- Person A then uses their own private key to decrypt the message.
- Person B‘s public key can be included in the return message or published publicly.
The efficacy of modern cryptography relies on the fact that certain mathematical problems are extremely difficult to solve. Such problems used are Prime factorisation and elliptic curve relationship; knowing this is not necessarily required to effectively use modern cryptography, but it is worth mentioning for those who may be interested.
A good analogy to this would be Person A sending Person B a lock-box with just a padlock, but no physical key. Person B then places a message inside the lock-box and locks it. From that point onward, Person A is the only one able to unlock the box with the key they have in their possession. Using this method, it is safe for anyone to have access one’s public key because all that it allows someone to do is encrypt messages to for that person. Only by compromising someone’s private key or failing to authenticate who you are communicating with will this secrecy and security be readily broken.
Now that there is a basic understanding of how PGP works, we will go through an easy method to implement it in email communications. Keep in mind that PGP will protect the privacy of communications, but not anonymity. An effective eavesdropper will still be able to know that you, Person A, has communicated with Person B. They will only be unaware of what is being communicated.
One of the easiest methods of setting up and using PGP is a browser plugin called Mailvelope. This is what I will be covering in the rest of the article. I suggest this because it does not require the installation of software to the PC, as it runs on the browser platform. This along with the fact that PC Email clients are in declining use is why I think Mailvelope is a worthy option. I will also link my public key and email at the end of the article, if you wish to practice sending and receiving encrypted email.
Mailvelope is currently only available for Chrome. It can be downloaded as an extension here: http://mailvelope.com/
Once you have Mailvelope added to your browser, a padlock icon will appear in the top right next to the Chrome settings button.
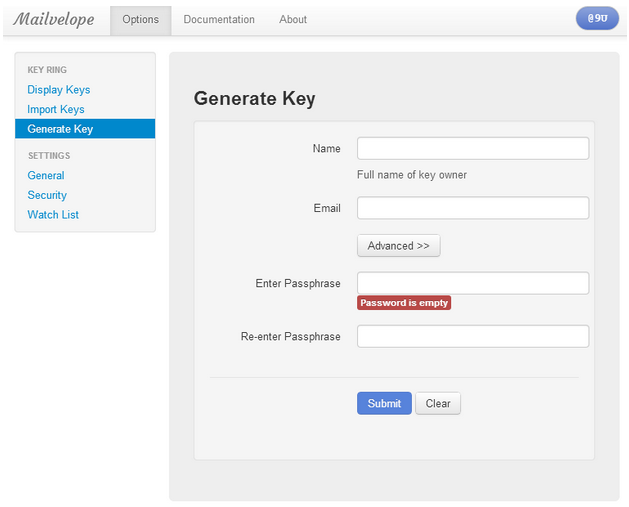
Left click on it and select “Options.” From here we need to generate a public/private key pair. This option will be in the left hand menu button.
Input your details in the fields provided. Make sure the passphrase you use is both long and something you can remember. If you forget this passphrase, you will no longer be able to encrypt or decrypt messages using that particular key pair. In the “Advanced>>” section, choose a keysize longer than 1024 bit for future’s sake. Once you have filled in the forms, click “Submit.”
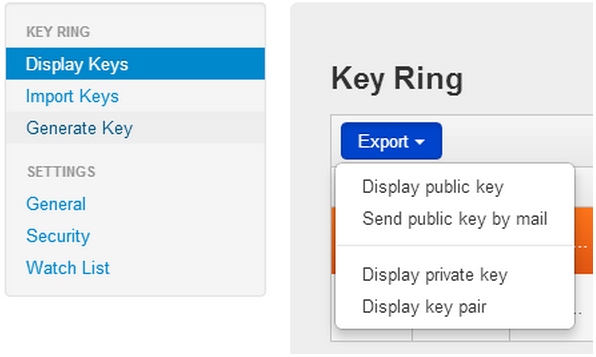
Once you have completed this, go to the “Display Keys” option in the menu. From here you can “Export” your public key. You can choose to send it to another PGP user via email or you can export it as a block of text and shared via other means. Do not give out your private key – ever. Your public key is totally public and can be safely shared far and wide or published anywhere without worry – as promiscuously as you like. All the public key allows someone to do is send a message to you.
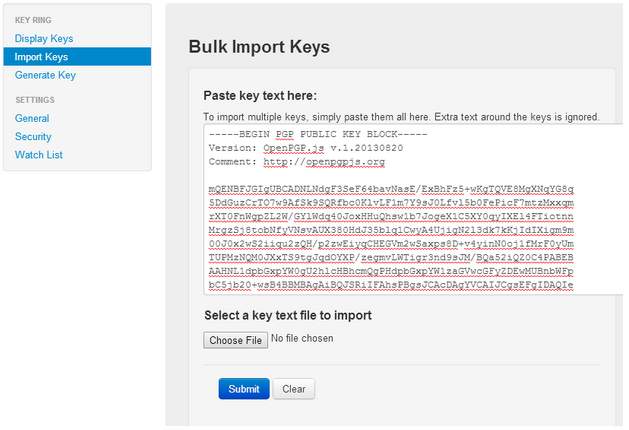
In order to send encrypted messages to others, you must import their public key. You can do this by importing an “.asc file” with the public key or copying their public key block. When obtaining someone’s public key, make sure you have, to the best of your ability, ascertained that who you are speaking to is really who you are speaking to.
Now that you have your keys set up and have imported someone else’s public key, you need to know how to send an email.
Open up your email client. Mailvelope comes configured to support Gmail, Outlook.com, Yahoo Mail and GMX. For this Demonstration I will use Gmail:
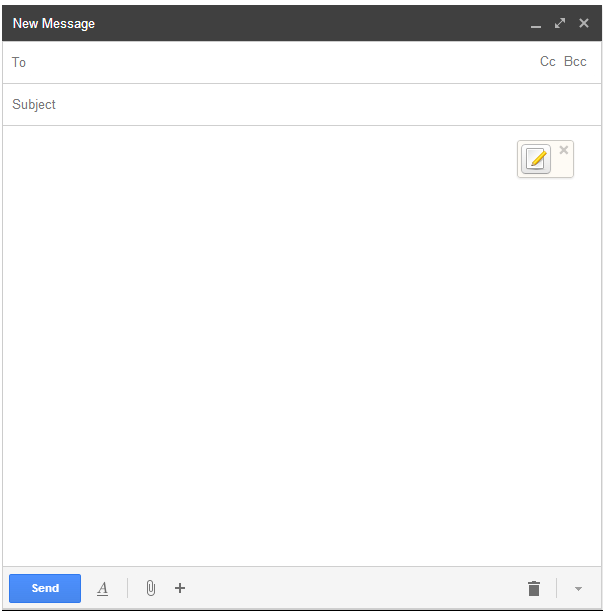
Go to compose an email. You will immediately notice a new “pencil and paper button” inside the compose box. First enter the recipient and subject, then, once you get to the body of the email, click this “pencil and paper button.”
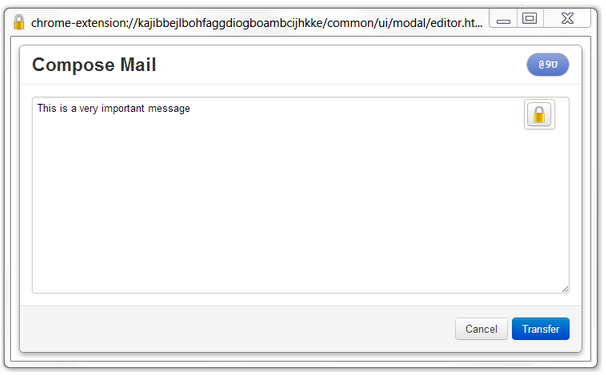
Compose the email in the box that opened up – this prevents clear text email from being automatically saved as draft by your email provider and potentially compromising the secrecy of your message.
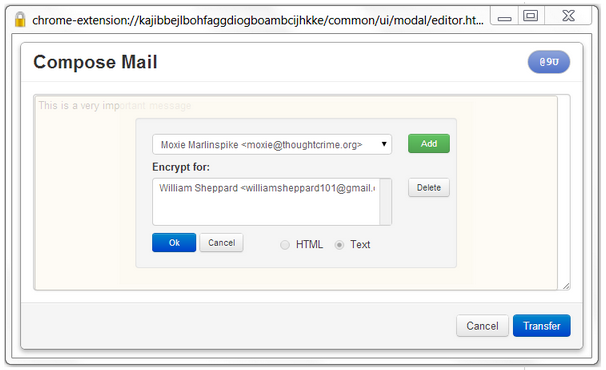
Once you have written your message, click on the “padlock button,” choose the recipient’s public key from the drop-down menu, click “Add” and “Ok.” You then press the “Transfer button” to move the encrypted text back to the compose box. Note that because PGP encrypts your message with a generated session key, then encrypts the session key with the recipient’s public key, it is possible to encrypt a message for multiple recipients.
An encrypted block of text will look like this:
—–BEGIN PGP MESSAGE—–
Version: OpenPGP.js v.1.20130820
Comment: http://openpgpjs.org
wcBMAxLijeXaycuCAQgAl8n4g5ilhHXKoAqawIxn/bT3i8cZ4HP6JxtCZWWM
rzjX75QFffr3U6OSByqpU+DRBmhd2zG0akzkImUqrkVmQbbZv4vqEpQMMwzh
heX+MuZeUCXKAWTCGfcIMbeXKjpuqbuL0F8NkHeAkqFJ8hcMY8aYX3VtaRbQ
oVdL5aPzMbS5kPxjtr1OY93dwy1jV7JvrYgpyuk4wpynfS1AfKpn2lDyCQGH
sTxu6yqrJUDnnYrs0TkgLvkPXueggA8+yw7zDd3iQ5P2VeMWHH7EAUa+gFj7
x/M3DtHsGvfdssiPP35PZrglHCsJGCTZScO+Re1M2IxZtnZNHfDU0V9lhX4i
Q9JQAQlHtm8etEXlyvovsXDfIE2SdKgcj1bgx359V+zZsvPNyOtqfYEuyszM
7i65cEqz9GdLGFusSYSFpespUCHC71zFmaHEGcmUpglLIvvX2W4=
=g9Kk
—–END PGP MESSAGE—–
You can now send your message knowing that if intercepted, it will be unreadable.
When you receive an encrypted email, Mailvelope will detect this and overlay a “padlock and envelope symbol” over it. Clicking on this “padlock and envelope symbol” will prompt you to enter your passkey. Entering this will display the message in clear text for you to read.
Now you should be fully capable of using PGP to encrypt and decrypt emails to and from your contacts.
If you wish to test Mailvelope out and don’t yet know anyone else with PGP set up, I have set up an email account to receive encrypted messages. The Email is: williamsheppard101@gmail.com
My public key can be found on the MIT server: http://pgp.mit.edu:11371/pks/lookup?op=get&search=0x12E28DE5DAC9CB82
I will respond to all encrypted emails I receive. Ensure you include your public key in the email.
Below are a number of other tools that are worth noting, if Mailvelope does not suit your specific habits or setup.
EnigMail for Thunderbird mail client
https://www.enigmail.net/home/index.php
A very clean and versatile addon for those who still use local mail clients, once it is set up it is arguably easier to use than mailvelope.
PGP4win
http://www.PGP4win.org/download.html
Comes with a number of utilities, including the certificate manager Kleopatra, which allows you to import and export encrypted messages, allowing you to copy send encrypted messages over other platforms.
GNU Privacy Guard
http://www.gnupg.org/download/index.en.html
For Linux users, GPG can be downloaded from the distro’s repository, or a source package can be downloaded from the website.
GPG Tools
https://gpgtools.org/
A PGP suite for Mac users.